A lot of ground has been covered sifting through all the revelations that Edward Snowden bestowed upon the world in 2013. From the secret courts that sweep phone records. The PRISM program explaining the close relationship between the NSA and tech giants. That the NSA was and probably still is trying to subvert current encryption and security. There was XKeyscore, a tool that allows it’s operator to search and target specific individuals and their activity. And how about “Tailored Access Operations”? The special government hacking team that infiltrated numerous computers worldwide with their exploits and hacker tools.
Regrettably, there were many documents that were leaked that when fairly unnoticed. Some rather damning material was secretly published by United Kingdom intelligence. A part of the intelligence coalition, the Five Eyes. The Human Science Operations Cell (HSOC) and Joint Threat Research Intelligence Group (JTRIG) of Great Britain’s Government Communications Headquarters published several particularly eye-opening presentations describing how they can destroy a target’s reputation. Although it is unclear exactly who a target can be, the materials reveals that the intelligence agency is mainly interested in going after supposed hacktivists.
Forget the fact that going after someone that hasn’t broken the law where you need to ruin their reputation prima facie seems highly illegal. Let’s focus on how they do it first. The following is a sample of slides from the the presentations titled “The Art of Deception” and “Full Spectrum Cyber Effects”, and “The Art of the Possible”.
The Art of Deception
The purpose of this publication is exactly in the title. This whole presentation takes into consideration all the work done with the Human Science Operation Cell. Where they dub psychology as “a new kind of SIGDEV”, or Signals Intelligence Development. With their research into human psychology, JTRIG can take advantage and exploit the information they have learned with real world and the cyber world techniques against unwitting targets.
In this slide they demonstrate the key skill strands; online human intelligence, influence & information operations, and disruption and computer network attacks. In every phase they have specific goals to obtain which also involve using persuasive technology, using the 10 principles of scams, and using propaganda with the media.
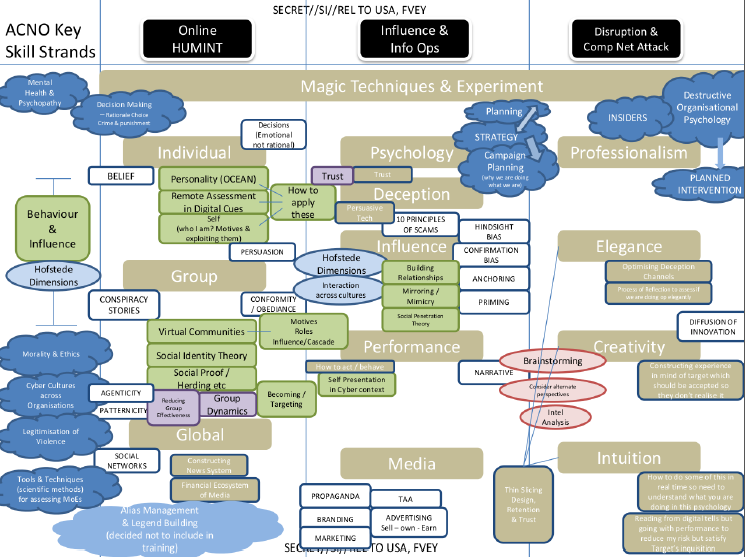
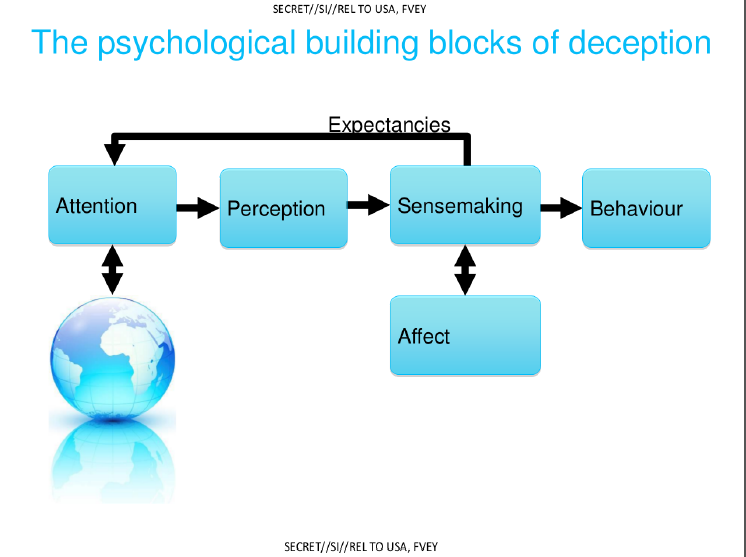
It would be interesting to hear the presenter’s comments on how building blocks of deception really works. This is a rather vague slide but informative on what they are trying to achieve.
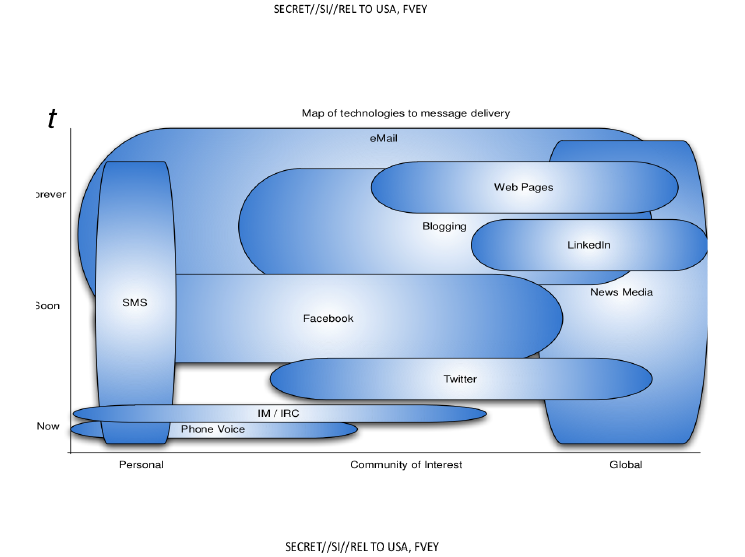
Here is a infograph on a road map to having capability with different interfaces to spread disinformation during a campaign. It is interesting that “News Media” and instant messaging is a capability they have had now and will have forever. This puts into question anything in the media when it is now a know fact that intelligence agencies use the media to present false information for operational purposes. Spreading their tailored messages by all these options is most likely on the table now as this document is wildly out of date.
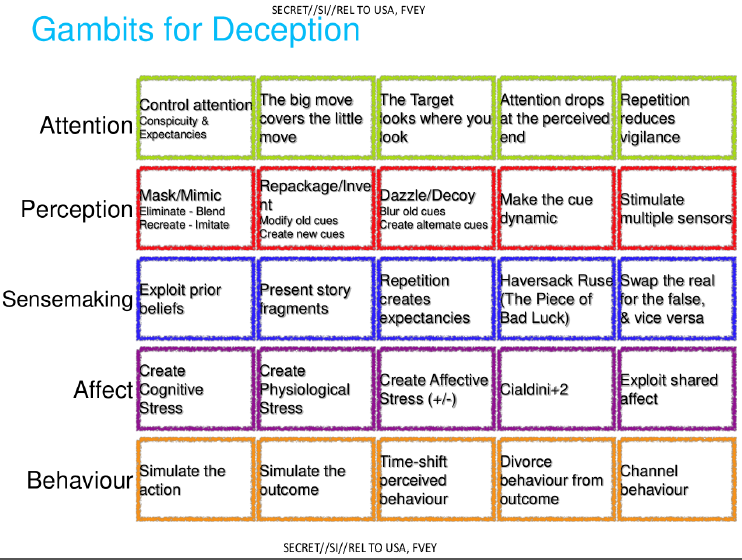
In case you didn’t know the gambits for deception. Here you go.
A rather troubling slide where the agency describes their disruption operational playbook. It is unsettling to know that there is a false flag operation in their tricks of disruption. Having that in there is a conspiracy theorists dream when it comes to any major attack worldwide and the motives of the attacker. There will always be the argument or question that it could be state sponsored terrorism.
What does it involve and what value does false rescue operations bring?

If the target is a group, no problem. With their psychological research they have identified how to destroy groups by pulling them apart. All they have to do is put into place techniques they know will create the tension or catalyst for destruction.
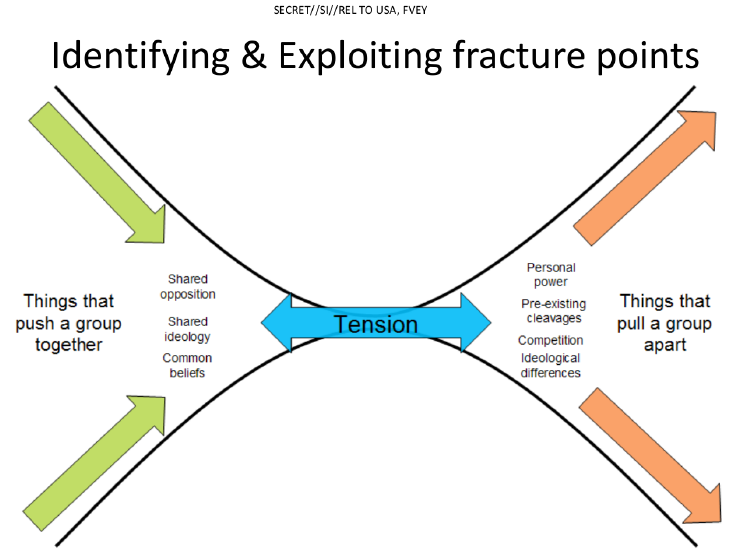
Other than the operation playbook that doesn’t get discussed more than a list of the operations, the Art of Deception doesn’t see all that bad. For an intelligence or spy agency, one would think nation states would need these types of techniques for spies to operate worldwide for threat intelligence. We have also known since the 1970s with Operation Mockingbird that intelligence agencies feed information to news outlets without anyone knowing or done wittingly by publishers. Although controversial, it is something most people already know about. On to current techniques. The next presentations get into even more unpleasant territory though, the previous skips detailing what the skill strand, disruption & computer network attack involves.
Full Spectrum Cyber Effect
This documents explains the GCHQ’s “Effects” mission. The effects consist of:
- Destroy
- Deny
- Degrade
- Disrupt
- Deceive
- Protect
It goes on to discuss the Computer Network Attack (CNA), the Computer Network Information Operation (CNIO) and Disruption. At the time of the slides, this consisted of 5% of GCHQ’s operations provided specifically by JTRIG. They boast of being able to distribute across all target types and they continuously innovate their tools and techniques.
Here they make no bones about it. They are using the major tech giants to push their CNIO which includes propaganda, deception, mass messaging, pushing stories, and more.

Their Disruption phase consists of masquerading their identity. No surprise there. Where it gets gray is spoofing and denial of service. Both cases in where a regular civilian would be committing a crime if done.

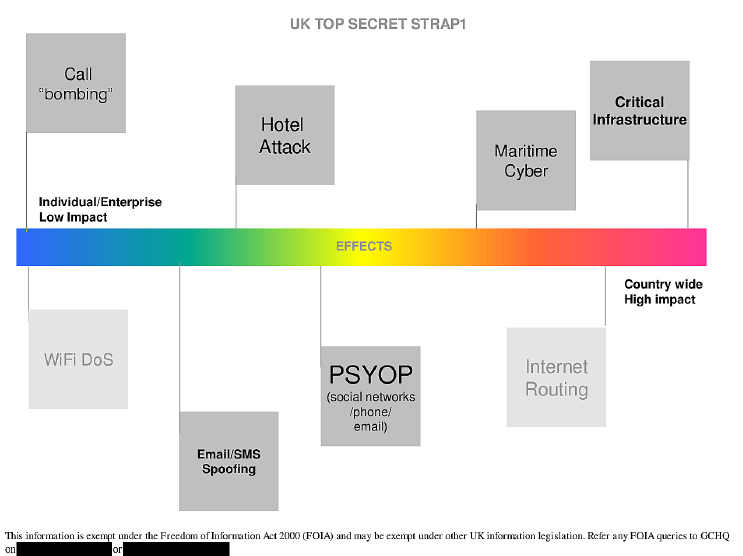
Here is a range of their “effects”. As low impact as “bombing” someones phone with calls all the way to disrupting critical infrastructure for high impact effects.
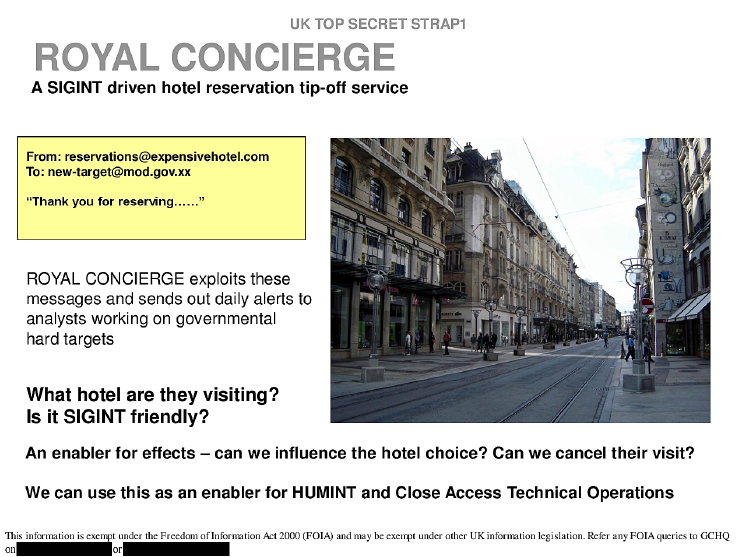
The operation, Royal Concierge, allows analysts to be tipped off when certain target arrive or makes a reservation with a hotel. It’s reasonable to thing a spy agency would want to know when a high value target arrives at a location. In this case, a hotel. There are legal means of doing this as part of an investigation but one would have to assume they achieve this through illegal mass surveillance. This alludes to intercepting email. Interestingly, they ponder if they can influence the target’s choice or cancel their visit all together.
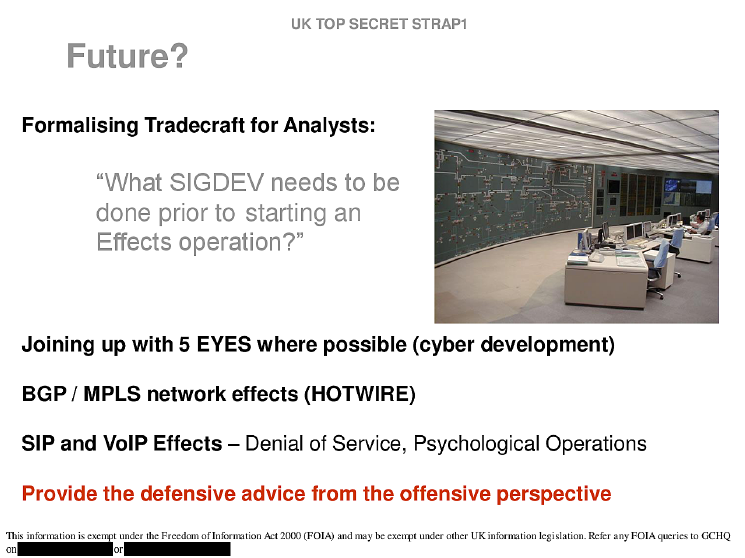
A slide at the end of this document seems rather innocuous. However, the bullet point that says “Joining up with 5 EYES where possible (cyber development)” is the terrifying notion that these techniques are or will be being used by Australia, Canada, New Zealand, and the United States as well. Not just the United Kingdom. Take note that some of these slides before being revealed allowed clearance from the United States already.
This is getting progressively worse, huh? Now we have more detail on how they are using their research into human behavior by applying cyber techniques. Furthermore, we now understand that they are using tech giants like Facebook, Twitter, Google, and Apple to spread their disinformation campaigns. There also is detail into the range of their targets, from individuals or enterprises to other nation states. Now we know they are willing to go as far as damaging critical infrastructure to get their “effect”. Oh, it gets worse.
The Art of the Possible
The following was a revelation exclusively from NBC News and Pulitzer Prize award winner, Glenn Greenwald. Without this document we would not be able at least have a gauge to identifying these attacks perpetrated on a target. The following slides demonstrate how intelligence agents can:
- Implant false information to totally destroy a person’s reputation
- Manipulate online discourse and people’s perception of people, places, things, or events.
Here it describes “effects”. To use cyber techniques to make certain things happen specifically through information operations and technical disruption.

Anyone can Denial of service attack by delete someone else’s online presence?
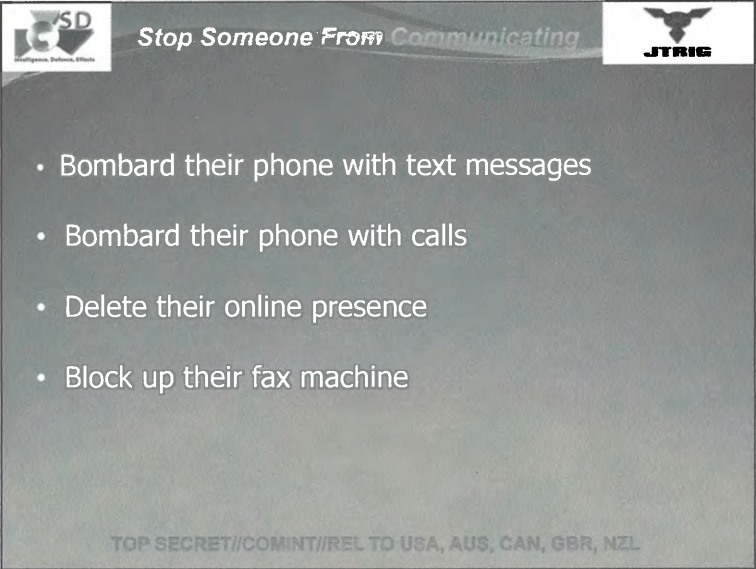
Yet another very disturbing slide.
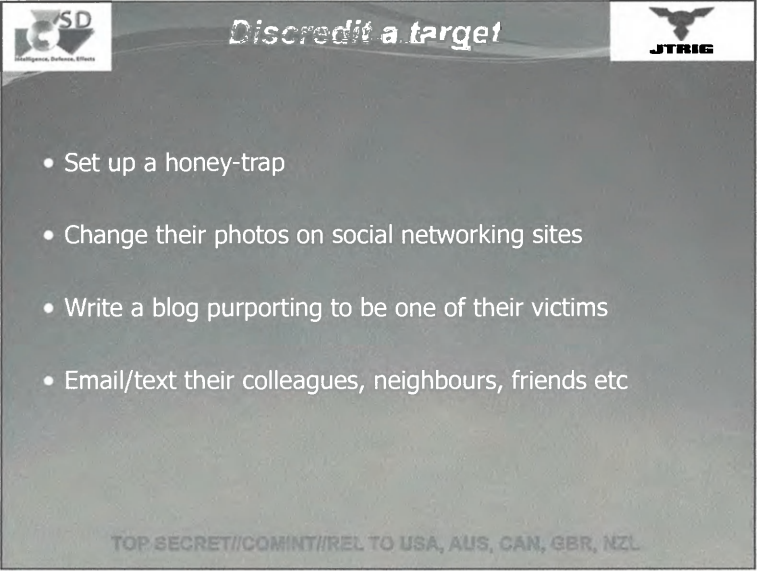
If you don’t know, a honey trap is a trap to get a target in a compromising sex situation. You don’t want those pictures getting out. For some reason changing their social media photos would have to include some sort of illegal hacking or access too. The third bullet point is especially worrisome as it exploits the victim role and has the potential for people not to believe actual victims. If this is intended for hacktivist targets, anyone being accused of harming anyone else in the information security space will seem suspect. The coordinated effort against Jake Appelbaum comes to mind. And when someone suspects they are a target of these campaigns, expect calls to your mom, dad, friends and co-workers to be told god knows what.
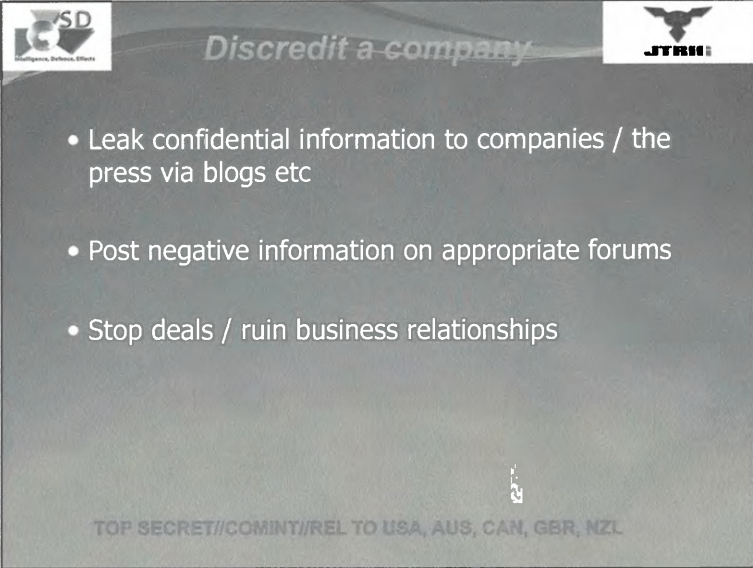
Maybe they really need to go this far on a certain target. This individual could be a real terrorist or cyber criminal, but they just can get with a warrant and charges yet. But here they admit they will discredit a whole company. One would assume they need to hack the company network to be able to get access to confidential information to be able to leak on them. If you ever had a untrue negative post about you or your company, you know how much of a dirty trick this is. Too bad we don’t have more information on how they stop or ruin business relationships, although one could assume it’s done through most of the other tactics.
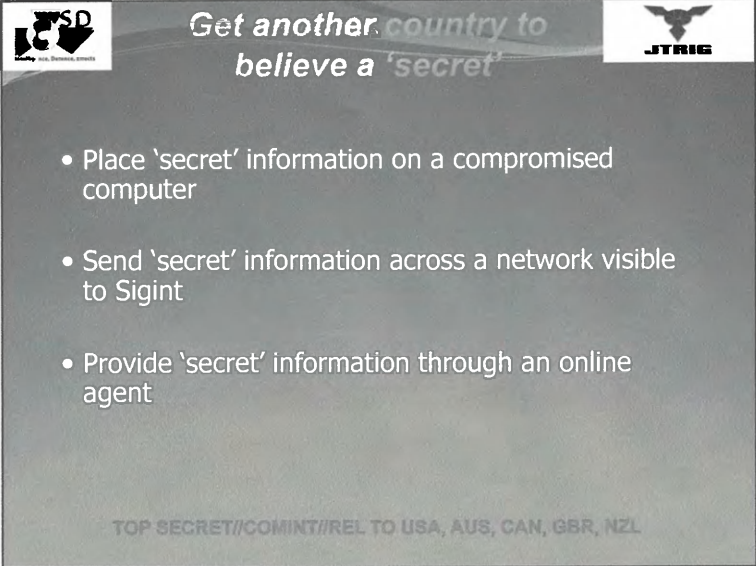
Not just businesses, state actors as well. A game of spot the bad intelligence.
Something you just assume is going on. No big deal here.
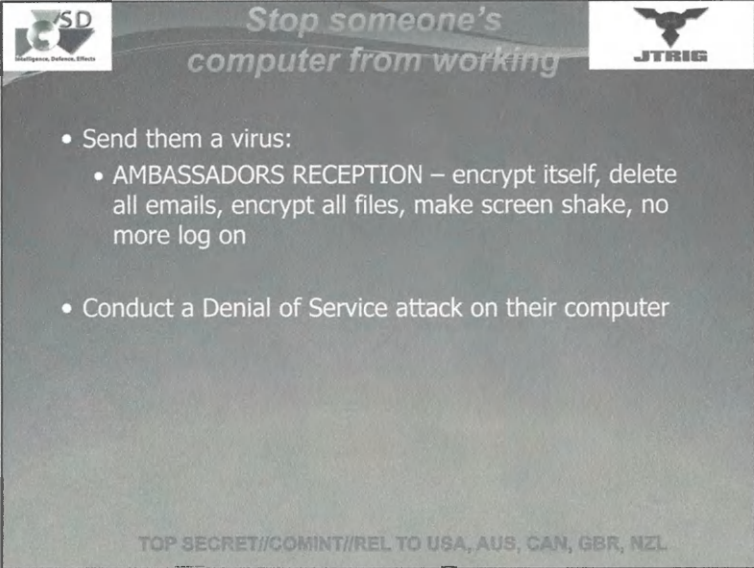
Want to shut someone down from doing their work? Just send them the confirmed virus, AMBASSADORS RECEPTION, to completely lock them out of their whole device.
Again, more illegal hacking and computer crimes. Or is this a line we cross.
In case you were wondering, two modes of impact.

As you can see now, this can get bad real quick. The most disconcerting aspect of this all is we don’t know what the criteria is to become a target of these operations. Although we know it can range from an individual to another nation state, no information has been uncovered to be able to know or get redress for the activities that could be perpetrated against you unlawfully. In most cases, you probably wouldn’t even be able to identify the actors involved.
Is this legal?
This is really murky water. When is it okay for our intelligence agencies to commit slander, defamation, lying, deceiving, and resorting to computer crimes. Let’s see what a regular citizen would be committing if they did the same thing.
There is no federal slander or defamation laws so these are usually the jurisdiction of the individual 50 states. There is no criminal law for defamation but a slanderer/defamator could be sued in civil court. However, since these are clandestine operations if the target is innocent they still would most likely not be able to uncover the agents involved to sue. Who would believe them anyways?
How about lying about being a victim of a crime or telling our family and friends lies about you? Can an law enforcement agency really lie to anyone in the course of their operation? Unfortunately, the case of Frazier v. Cupp 394 U.S. 731 (1969) allows an agent to lie to you. Although it applies mainly to questioning and interrogation, its could be assumed this could apply here too albeit an outrageous legal argument.
Most of the hacking laws are covered under the Computer Fraud and Abuse Act. For the most part , law enforcement is held to the same laws. However, in some cases, particularly during the investigation of a suspect and crime, they are able to perform network investigation techniques which involves malware and hacking. But this means a warrant has to be attained and a reasonable suspicion of wrongdoing must be involved. Learn more about warranted law enforcement hacking in my article about Rule 41.
How can you become a target?
Since there is no criteria for you to become a target of one of these reputation destruction campaigns, who gets on the list. Apparently, you don’t have to commit a crime or be suspect of a crime. Which is the scariest of all. If you are an activist, or anyone that disagrees with what these intelligence agencies do or say, you could fall victim to some of the dirtiest tricks known out there and you wouldn’t have any way to fight back. You may not even know and if you find out there is very little you could do about it.
It leads to the obvious question to this whole thing. If the target is so dangerous, why are they trying to ruin their reputation instead of bringing them in on charges? How many lines where crossed for someone you can’t even pick up or get a warrant for? Most people would agree that we need these intelligence organizations. They keep us safe from threats diligently on an ongoing basis. But what do we do when they betray our trust? If they are performing these campaigns against people they can’t put in jail, spread false information to the media or hack into any computer system known to man…. what can we believe from them anymore?

Hi Michael. Thank you for writing this article. I have a whole experience of dealing with this sort of thing and it’s gone on for years – JTRIG.
I have a major problem where it’s been a case of trying to help those who are suppose to know these things get a full grasp of understanding of the things that are involved in this type of thing. Not sure where you could got your information from but I need your help, possibly.
I need you to contact an organisation that is suppose to work with the public when dealing with racism and issue related to the police – undercover police, operations, surveillance etc.
The organisation is based in the UK – SPYCOPS. It’s pretty intense but with your help, possibly, it might be something that can be explained further so as to give them guidance on what they can do or help with.
I am someone whose been vocal about a number of topics which includes black lives ( along those lines), humanitarian issues and more.