It’s unfortunate but people get scammed online everyday. These scams pull in millions of dollars a year. Keeping that in mind, it doesn’t seem like these cyber criminals will stop anytime soon. There are the Nigerian emails scams claiming to come from a dethroned prince asking for bank account numbers. Some scammers are egregious enough to masquerade as the IRS threatening jail time if you don’t pay them money. The most popular scam is a alert pop up which locks your screen and provides a number for IT services.
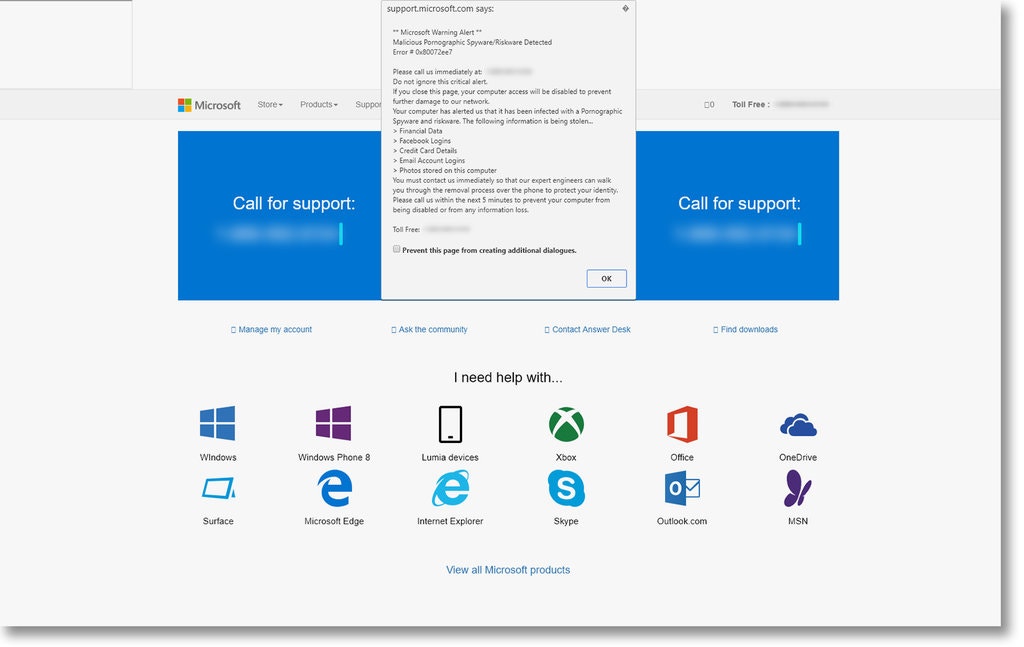
This scam draws a lot of attention from people as the individuals that fall for it typically will be a grandma or grandpa that isn’t really tech savvy. Most of these calls come from large call centers usually located in western India. They usually provide fake American names and attempt to gain remote access by getting a victim to install remote access software to connect. Once connected there is usually a script they go through to convince the individual that they have been “hacked” and that the system needs “security tools”. They do this by running typical built in system administrator tools in Windows and lie about the results the tools provide.
Tricks of the Trade and what to look for
Many of these IT call center scammers have a number of techniques they use to trick the victim into coughing up hundreds of dollars to fix the computer. Here are a few.
One of the most typical is running the Tree command. This command is nothing more than a recursive directory listing. Since it takes a bit of time to run, the scam operator can type what ever they want while it is running and it will be typed at the bottom after the command is done. This can make it look like the actual program produced the output.
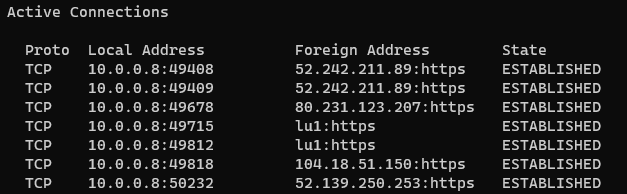
Although laughable to IT technicians, the next trick they use is the Netstat command to convince the victim that hackers are connected. In reality, the active connections shown from the command are generally regular connections by a web browser or the actual remote access software connecting back to the scammer. So when they say a hacker is still connected to the victim, they aren’t lying for once!
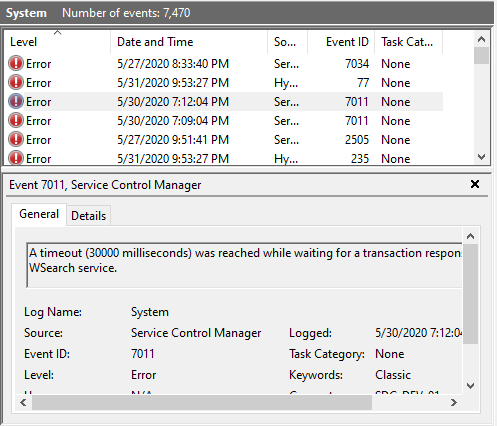
One of the most convincing techniques a scammer will use is the Event Viewer tool. This is Window’s main logging system for information, warnings and errors. This helps administrators pin down issues on a computer. It’s inevitable that Windows will generate errors in these logs but the scammers will point to the error and give an outlandish reason for it being there, such as hackers have gotten onto the system.
There are many other tricks up their sleeves. But typically these routines will always be used first. If you find yourself calling a company thinking they are Microsoft to fix your computer and they try these, look out!
If you’ve seen a demonstration of how these call scams work on YouTube, you know how ruthless these people can be. They usually have no issue scamming an elderly person out of hundreds of dollars. Or making them go to the store to purchase gift cards in the middle of the night, a currency they typically use if they are not able to function with a proper credit card payment system.
In the worst case scenario if the call doesn’t go the way the scammer wants it to, usually ending in payment, they will go ahead and delete files, apply actual viruses to the computer or lock them out with Microsoft’s SysKey. Which means the victim would need to know the password the scammer put in to even start up the machine. Luckily, the SysKey program is now unsupported in Windows 10 and later.
Fighting Back
Even though these scams have been perpetrated for years and years, it still happens frequently. Old scam sites go down and new ones pop up. And since most of these call centers are overseas and targeting Americans, these isn’t much the average citizen can do to stop it. Meanwhile, more and more grandparents are getting fooled out of their hard earned money by these scams.
However, many have found a way to fight back. By calling the call center up and allowing a potential scammer to log into their virtual machine. From their standpoint, there is nothing they can do to a virtual machine that can’t be fixed by a snapshot revert and any wasted time with them is time not spent targeting an actual victim. For some of these outraged individuals, they have made a living demonstrating on YouTube how these scams work in very entertaining ways.
Here are some good channel’s to watch on the scam process.
If this is something that intrigues you or you were drawn by the title, here is how you harden a virtual machine to bait a scammer yourself. Astute scammers are now looking for identifiers that the machine they are logging onto is a virtual machine. A result that usually ends the whole scambait adventure real quick.
Continue on to learn how to keep the adventure going all the way through. How you play your adventure after that is up to you!
Hardening The BIOS
As scammers are looking for virtualized environments, we need to spoof parts of our hardware to keep the bait going. First we need to spoof the BIOS. To do this we need to use @JayMontana36’s vBox System Info Mod to update our VirtualBox virtual machine.
You can download from his Github account:
https://github.com/JayMontana36/vBoxSysInfoMod/releases
Unzip, run the executable, and run the “ModifyVM” command. Then finish the rest of the questions asked. Make sure you select the right virtual machine you will be using as scambait.
Configuring the registry
Now start up your victim machine so we can configure more settings.
Next we need to change the name of our system devices with Regedit. Open up Regedit and locate the following key folder location.
Computer\HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Enum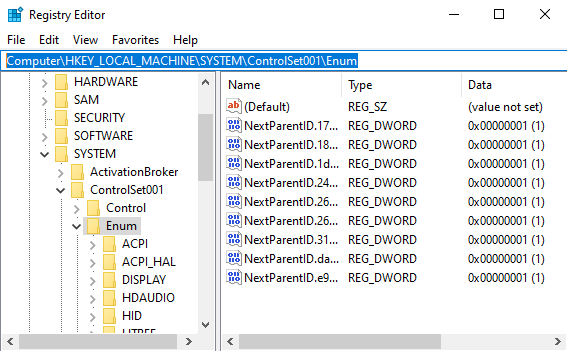
Next right click on “Enum” and click “Find”. Search for the following identifiers.
{4d36e967-e325-11ce-bfc1-08002be10318}You will need to change the FriendlyName for the hard drive. Right click on the entry and change to a realistic equipment name.
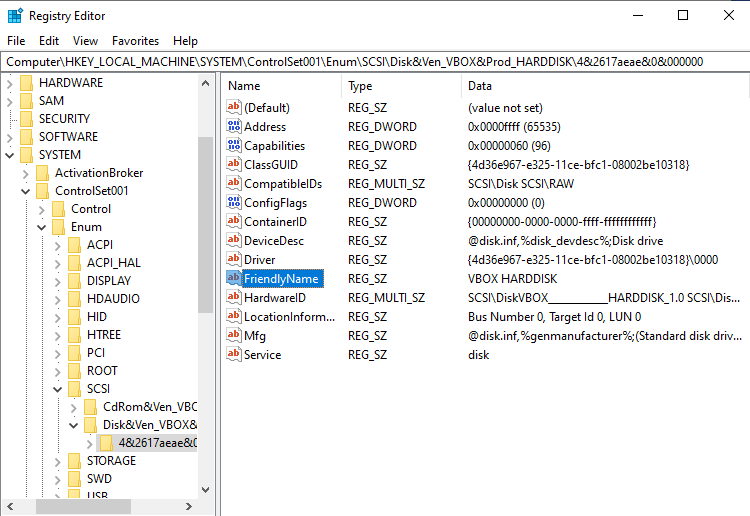
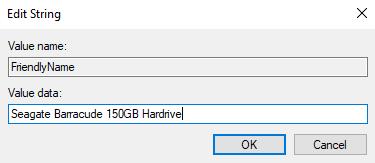
As you can see in Device Manager, the generic name of our hard drive has changed.
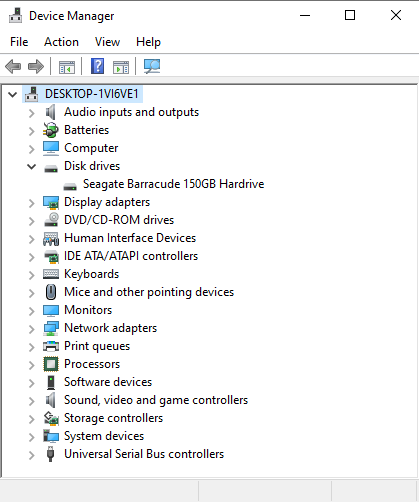
Now we can go ahead and change the rest of the names of the hardware that will tip off a scammer. Find and change the rest with the same process.
The next is for our virtualized graphics card. Unlike our hard drive, we will have to change the name in the DeviceDesc key instead. Since VirtualBox pulls in information from files in this entry, we need to clear the whole value data. Then put the spoofed equipment name.
{4d36e968-e325-11ce-bfc1-08002be10318}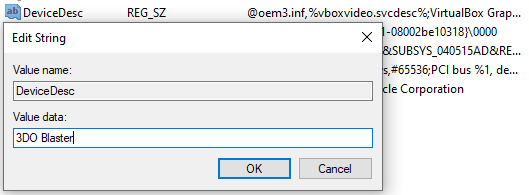
3DO Blaster hasn’t been around since 1994 but since this is adventure, let’s make a joke of it. Fortunately, for us the scam operator will mostly be looking for VMWare or VirtualBox in Device Manager so we can keep this inside joke.
Now change the CDROM drive name. We can use the FriendlyName entry since it’s available.
{4d36e965-e325-11ce-bfc1-08002be10318}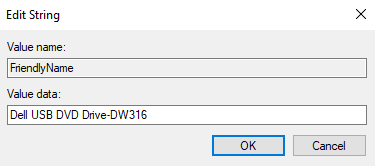
Now change the mouse name in DeviceDesc key in the following folder.
{4d36e96f-e325-11ce-bfc1-08002be10318}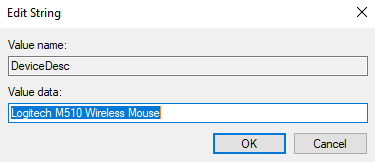
Cleaning up
You most likely have VirtualBox Guess Additions installed on your VM. If you go to Programs and Features, a location a scammer has to potential of checking out, it’s listing is sitting right there for them to see.
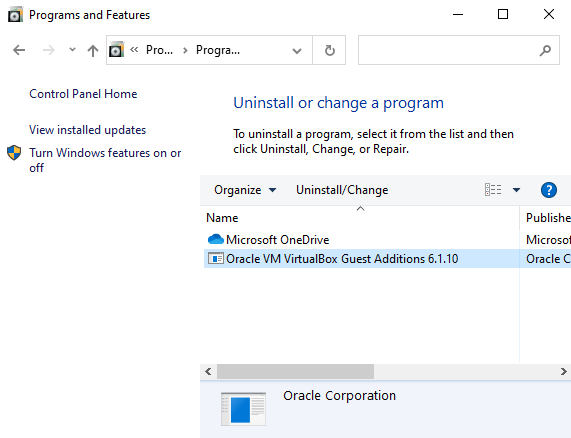
We need to delete it from the listing. To achieve this, we have to delete in the Registry. Go to the following location in registry and delete the VirtualBox folder. If you want to update the guest utilities, make sure you export the folder first so you can restore it later.
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall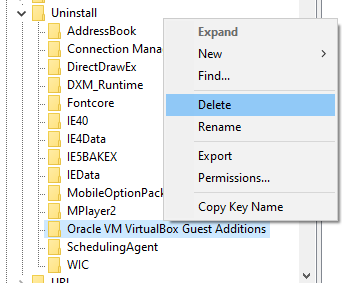
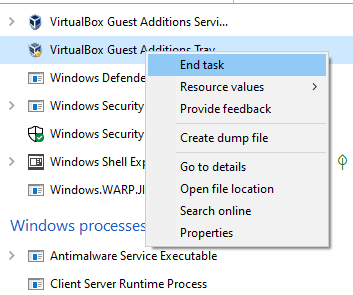
Now all we have to do is get rid of the pesky VirtualBox icon in the VM’s taskbar.

Currently, there is no way to permanently remove this from the taskbar. In order to remove it temporarily, you will have to shutdown in task manager. Right click on the taskbar and click “Task Manager”. Look through the processes and look for “VirtualBox Guest Additions Tray”. Then right click and “End Task”. You will have to do this before every scambait adventure so the scammer doesn’t get tipped off right after logging into your VM.
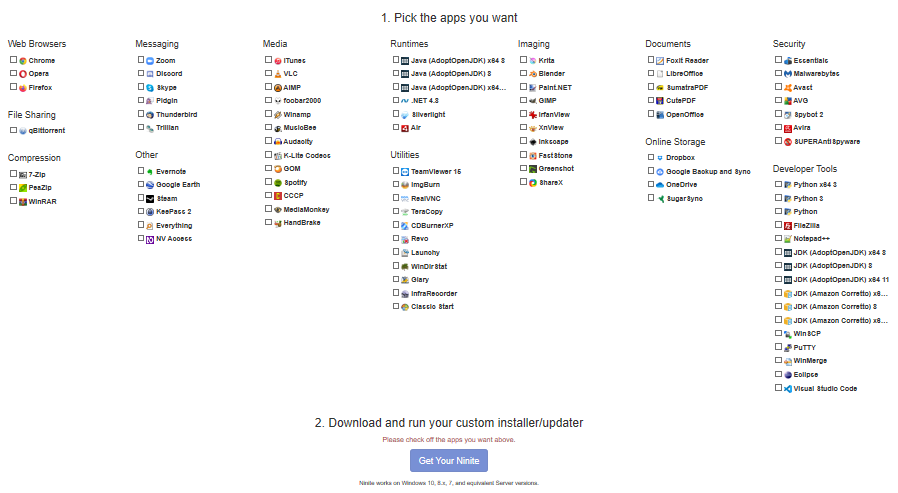
Lastly, you will probably want to load up the VM with a bunch of software to look like a normally used computer. We can do this the simple way with Ninite.
Let’s head over to Ninite now. Select the applications you want, and hit “Get Your Ninite”.
You are all set to bait your first scammer! All you need now is a number, a VPN, and a VOIP solution to stay as safe as possible. I will leave that up to you.
Helpful Links
If you are looking for good links to find new scammers on the market, look no further.
What you do from here on out is up to you! Enjoy your adventure!

Comments are closed, but trackbacks and pingbacks are open.