So you need a key asset’s email, but it doesn’t seem to be publicly available. At least it sure isn’t on the organization’s website. You could be performing a network penetration test against that corporation and need to leverage a spear fishing attack. Or you could be a salesman looking for an email to send information before conducting the cold call. So what now? Is there another way to perform more reconnaissance before we either call or give up?
Welcome open source intelligence gathering.
So you need that email but you looked all over. If this wasn’t your first step, it should be your second to use the free and open source application, theHarvester. Although this tool is mainly purposed for penetration tests it can also be used for everyday use. You can put it to work to collect emails, names, domains, IP addresses, and URLs. theHarvester utilizes over 30 different search engines to gather information on a target. You can configure to search Google, Bing, DuckDuckGo, LinkedIn, Netcraft, Shodan, Trello, Twitter, Yahoo and more.
Continue on to learn how to install and use theHarvester.
Installing theHarvester
To use theHarvester, you will need the following prerequisites:
- Python 3.7+
- Pipenv
- Git
Install the above packages with your operating system’s package manager. Unfortunately, theHarvester does not run on Window’s as the Uvloop Python package it depends on is not compatible. As a work around, you can still use a Linux distribution in Window’s subsystem for Linux. You can learn how to install Kali Linux on Windows in my article here.
# Linux
<apt|apt-get|dnf|pacman> install python3 git
# OSx
homebrew python git Now that we have the prerequisites we can fetch theHarvester with Git and install the Python dependencies.
git clone https://github.com/laramies/theHarvester.git
cd theHarvester
python3 -m pip install -r requirements.txtStart up theHarvester by executing it’s Python script.
./theHarvester.py
If you got this screen banner, theHarvester is installed correctly.
Searching organizational information
To demonstrate how theHarvester gathers information, I will target my own company, Sof Digital, to see what information comes up. Typically you will be using the following command for your general searches. Here we search the target organization’s domain with the d flag. Limit our searches to 500 with the l flag and utilize Google for our search through the b flag.
./theHarvester -d <domain.com> -l 500 -b google.comThe results of the search:
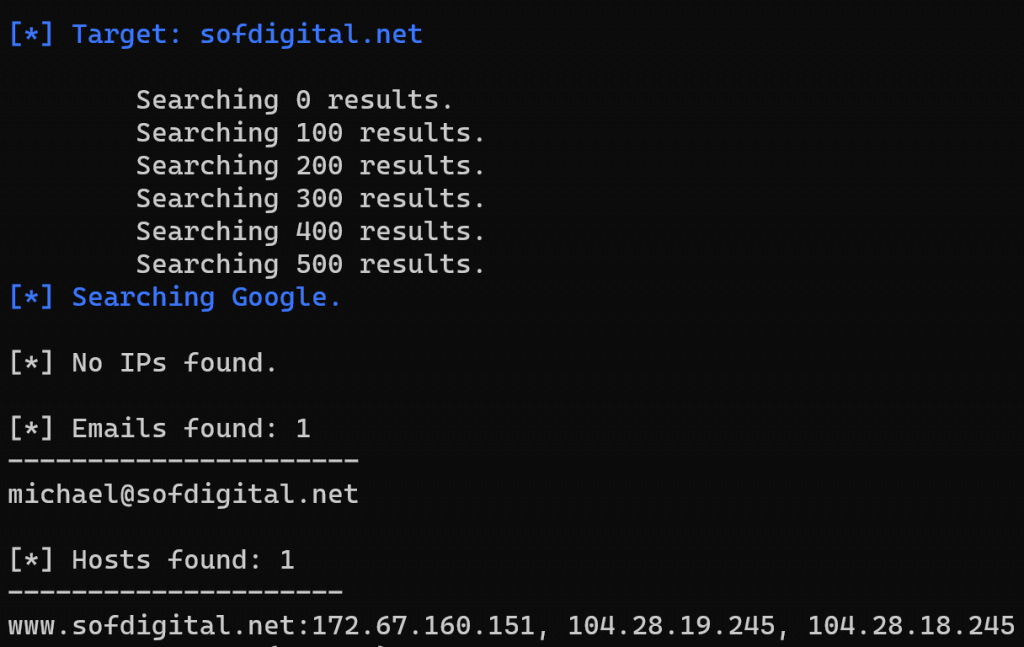
Great! We got the key asset’s email! We also found the IP addresses of my organization’s web servers. At this point, we can now use this information to leverage an attack on the key asset or start our cold call to the individual with a email prior to the initial contact. It’s that easy to scrape a specific search engine for all that organization’s email contacts.
We can even search PGP servers for emails with the pgp setting on the b flag.
./theHarvester.py -d <domain.com> -b pgpIf the results are lacking, you can just try all the search engines with the all setting.
./theHarvester.py -d <domain.com> -l 500 -b allIf you want a nice HTML page for your results, you can apply the following command. Then open up the file in a browser.
./theHarvester.py -d <domain.com> -l 500 -b all -f results.html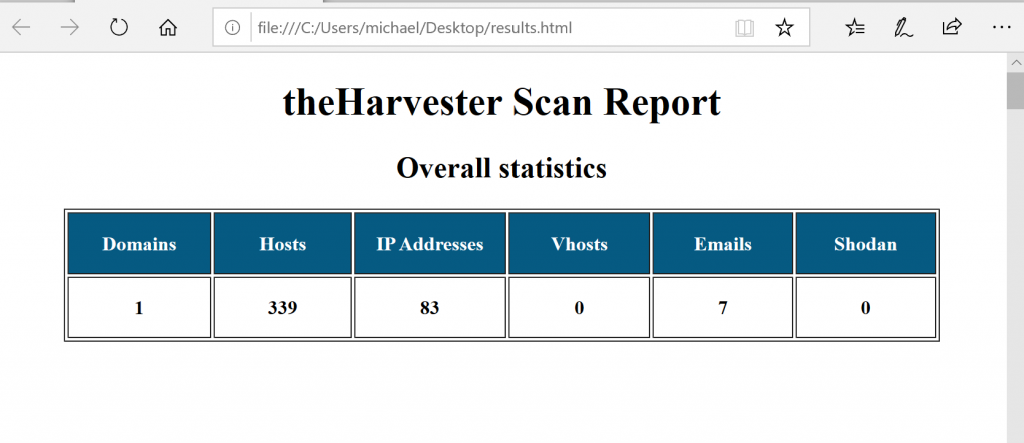
Wrap up
theHarvester is always my go to for email reconnaissance and for good reason. It automates searching for an organization’s information in minutes across tens of search engines. If you haven’t tried this tool before, hopefully this demonstration shows you the power of theHarvester and open source intelligence gathering. Now you have no reason not to find that email if it is public on at least one place on the internet.

Comments are closed, but trackbacks and pingbacks are open.