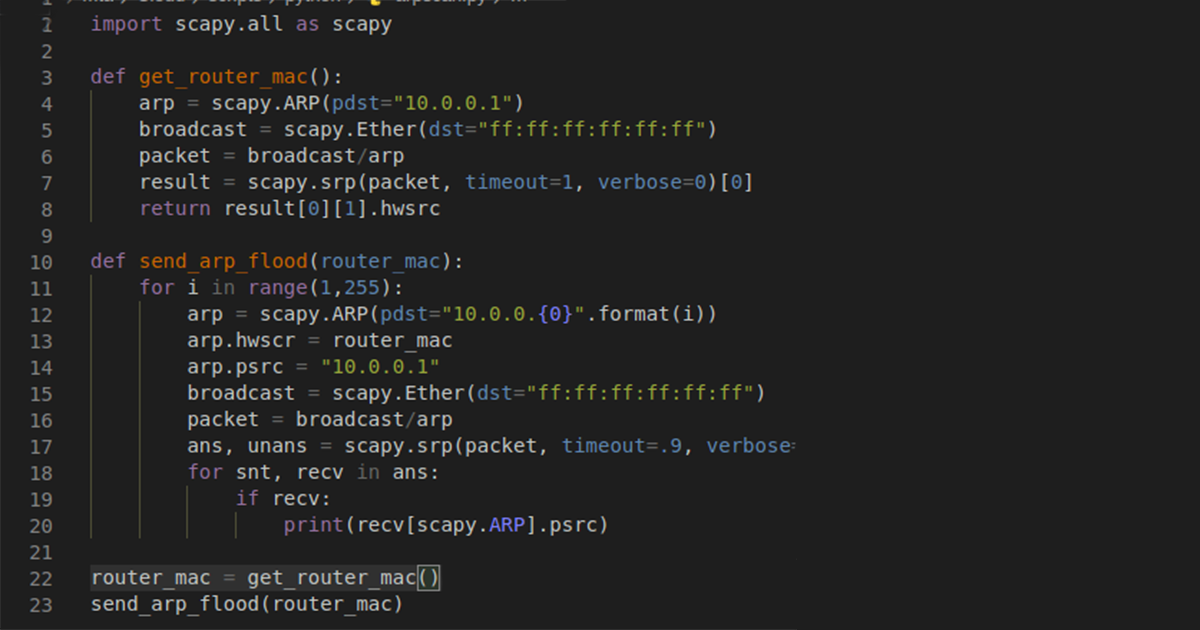
We often forget about our trusty routers on our networks but they are always working as a first line of defense against the internet. Without…
Category: Linux
It is not a widely known fact but the Linux operating system runs pretty much all the services on the internet. Nearly 97 percent of…
Most systems do not hold user passwords in clear text. Best practices for password storage is passing it through a hash function that creates a…
For most of us the name Phil Zimmermann doesn’t ring a bell. But it was his software and legal battles stemming from creating it that…
When an attacker has gained access to a private network the next goal is to look around the network to see what is on it.…
Ever since the first version of the Windows Subsystem For Linux (WSL), people have been seeing major benefits of the feature in the Windows ecosystem.…
Can you scan the entire internet with over 8 billion devices connected to it? In the event of a newly found major security bug, researchers…
Some projects require tunneling through a proxy system to connect to, monitor or probe a specific resource. If you are programming with Python sockets you…
Bulletin board systems have been around longer than most of us can remember. Some were not even born yet. Nevertheless, when most people didn’t even…
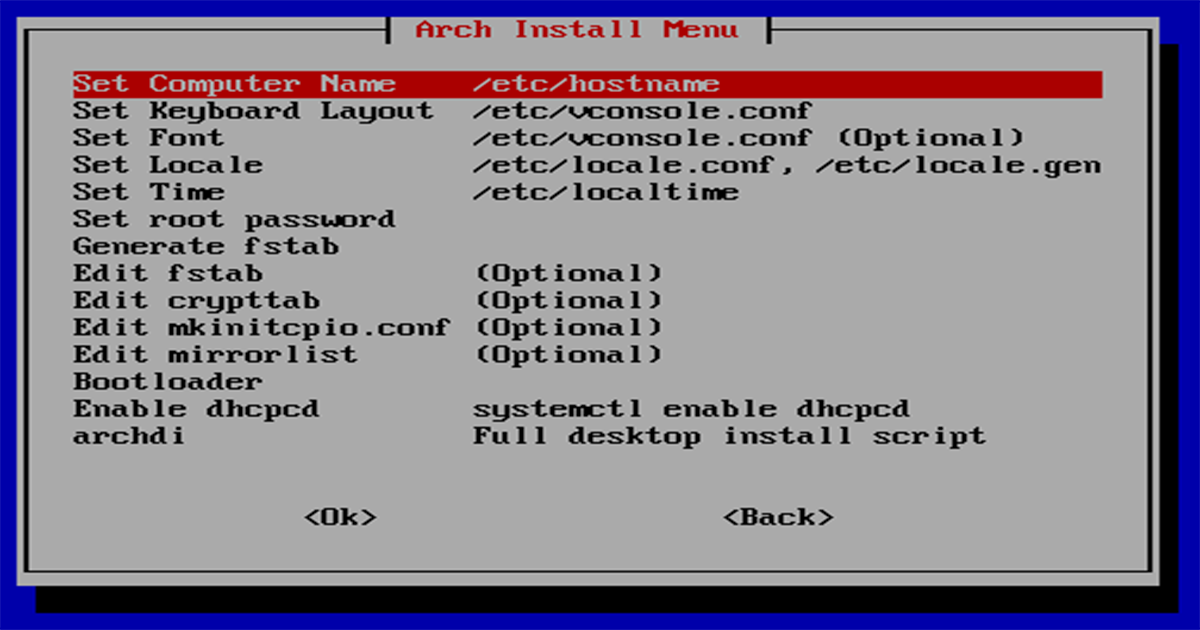
The biggest complaint about Arch Linux is that it is very difficult to install. However, there is an option that makes the process an absolute…