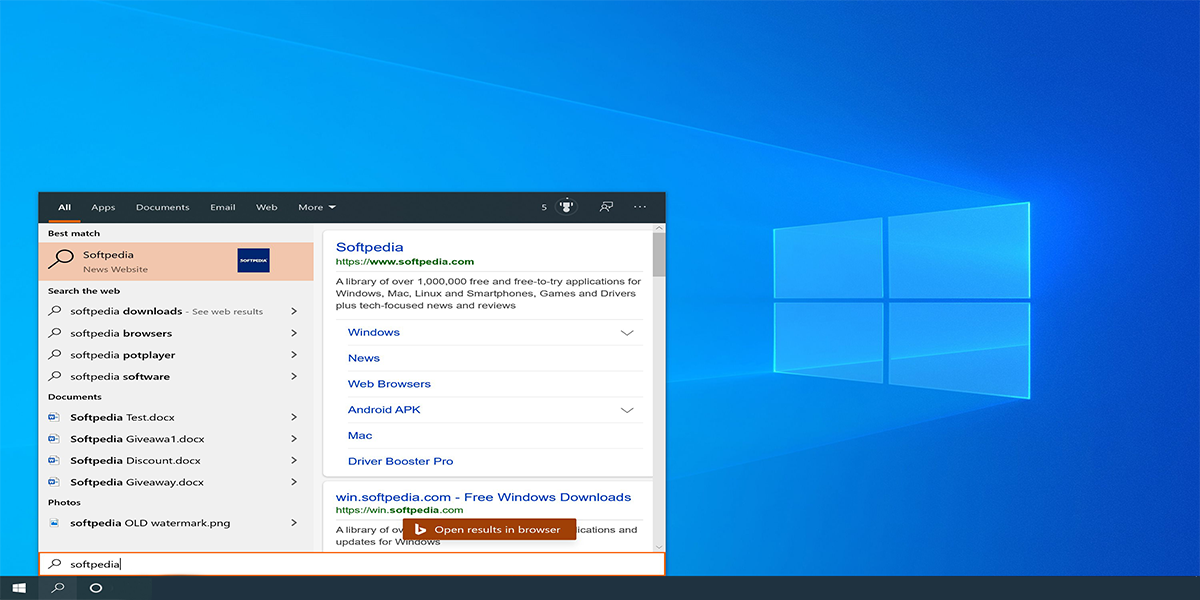
If you didn’t notice, by default Window’s search feature from the start menu leaks your data. Each and every time you type a search from…
Category: Windows
For most of us the name Phil Zimmermann doesn’t ring a bell. But it was his software and legal battles stemming from creating it that…
If you think parental controls are dead, think again. Today I will provide you with a way to protect your family by configuring your device’s…
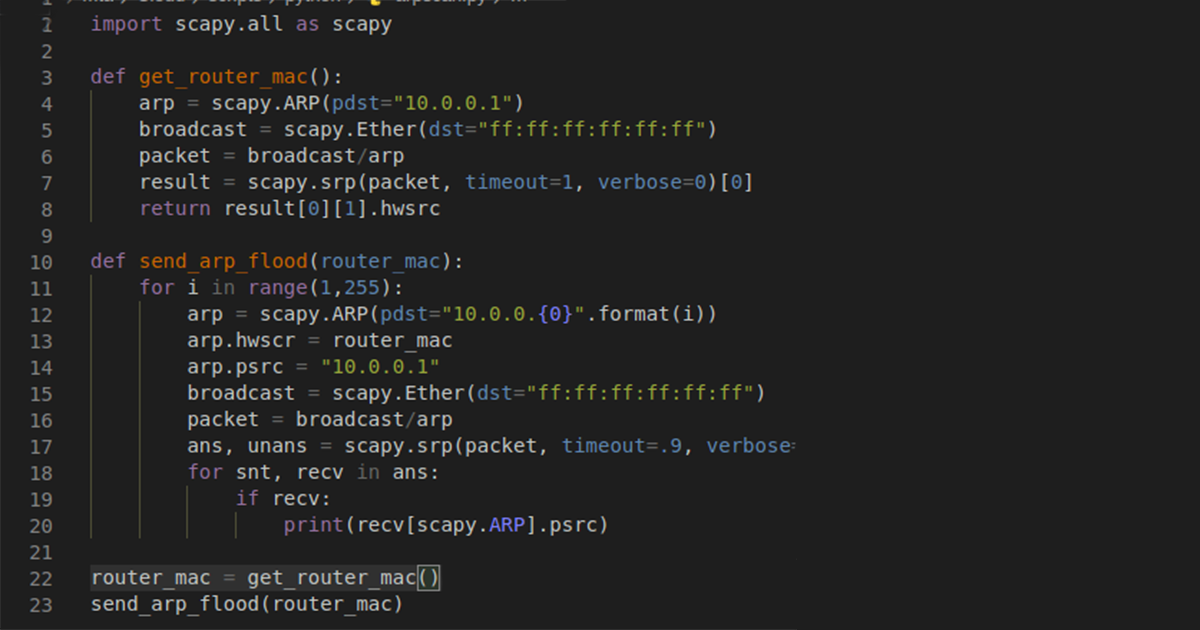
When an attacker has gained access to a private network the next goal is to look around the network to see what is on it.…
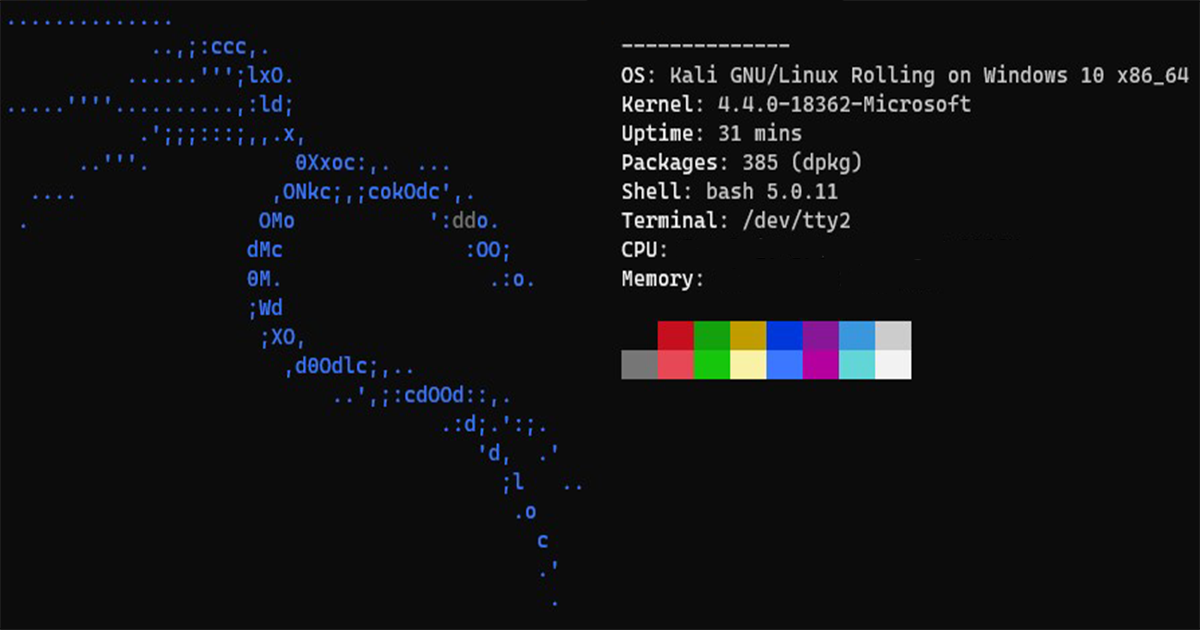
Ever since the first version of the Windows Subsystem For Linux (WSL), people have been seeing major benefits of the feature in the Windows ecosystem.…
Can you scan the entire internet with over 8 billion devices connected to it? In the event of a newly found major security bug, researchers…
Some projects require tunneling through a proxy system to connect to, monitor or probe a specific resource. If you are programming with Python sockets you…
When referencing a class library .DLL file in a Visual Studios project you cannot break or step into your class library code right out of…
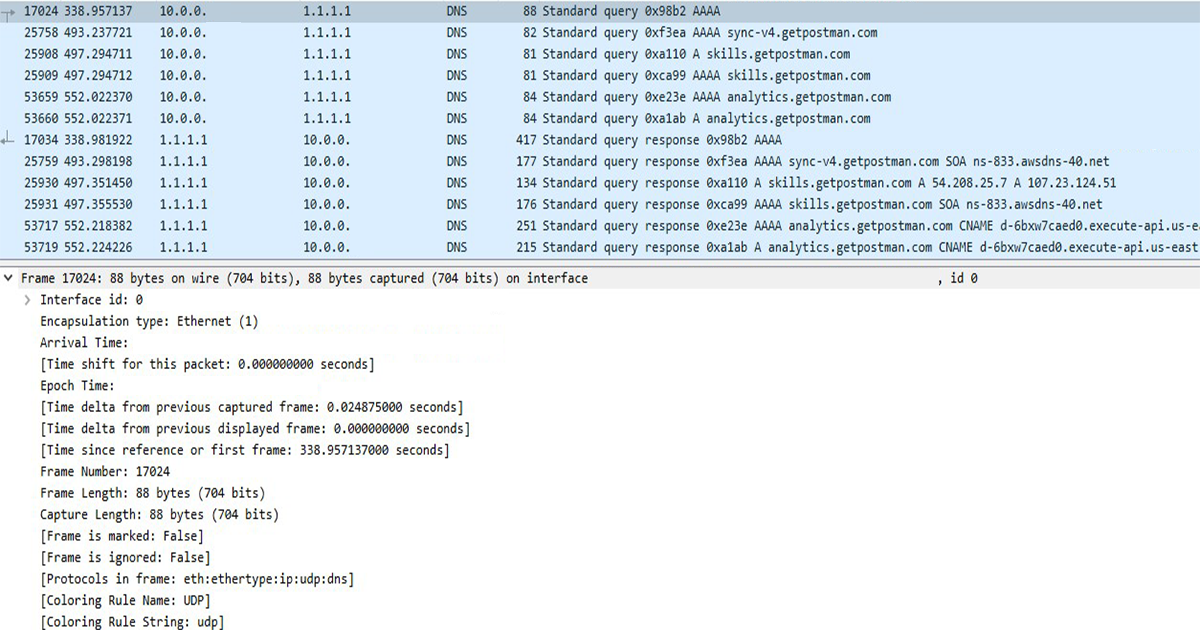
Your web history can easily be tracked. The internet is connected through Internet Protocol addresses. Each device on the internet communicates through these unique addresses…
Most people think they have a reasonable degree of security when it comes to Windows 10. Yet even today, Window’s Defender cannot stop a simple…